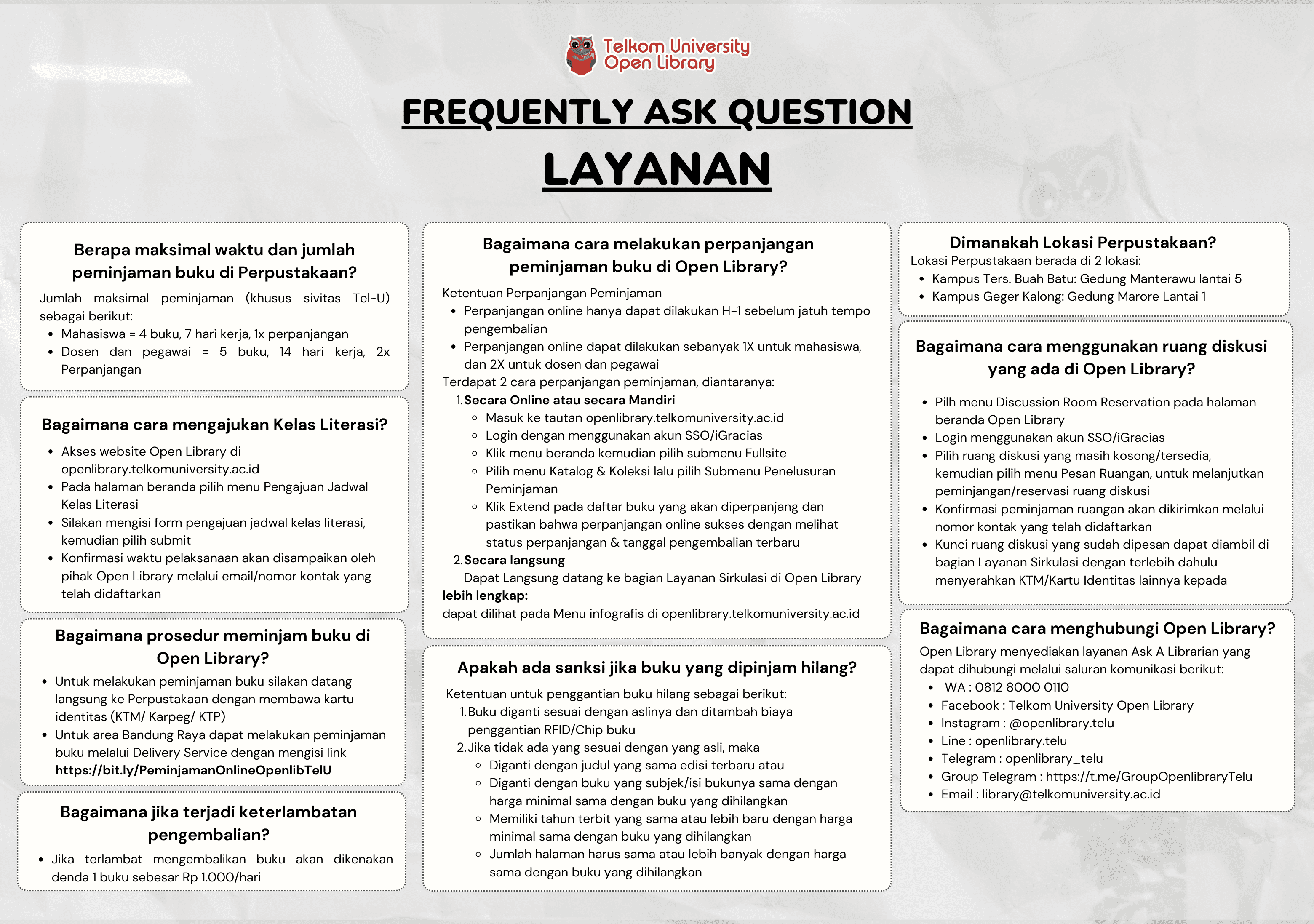
ASSESSMENT ON STORAGE AND FABRIC LAYER OF STORAGE AREA NETWORK INFRASTRUCTURE
BUDHI HAMDANI

Informasi Umum
Kode
17.05.070
Klasifikasi
621.3 - Electrical, Magnetic, Optical, Communications, Computer engineering, Electronics, Lighting
Jenis
Karya Ilmiah - Thesis (S2) - Reference
Subjek
Computer Security
Dilihat
227 kali
Informasi Lainnya
Abstraksi
Storage Area Network (SAN) has become standard infrastructure in various IT-aware companies. Mutual use of SAN and virtualization software becomes unique attraction for many companies since it offers lower cost in IT expenses, compared to traditional use of server infrastructure. Reviewed from security aspect, the use of SAN is relatively secure since connection between host and storage layers uses different protocol (fiber channel) separated from TCP/IP. For common user, this will make it harder to conduct attack or data-stealing. Nevertheless, SAN infrastructure has a weakness that holds potentials to become entrance for data-stealing or attack, impacting in total paralysis of SAN infrastructure. The weakness point resides in services provided by each component layers of SAN, i.e. storage and fabric layers. For the convenience of SAN infrastructure management, services are provided both web-based and shell-based (command-prompt). These two services are the entrance gate to SAN infrastructure. In this research, a penetration testing for Denial of Service was conducted on services provided on storage and fabric layers commonly used in SAN infrastructure management, in order to test the resilience of operating system implemented in those layers. Result shown that management storage and fabric layer susceptible to denial of service attack.
To solve this problem, ssh tunneling became one of the answer. In this research SSH tunneling system proposed as intermediary system to forward access from client to storage and fabric services. In this scheme, client and attacker does not have direct access to storage and fabric services, but accessing the services through tunnel was created by ssh server.
The proposed ssh tunneling scheme give better performance compared to system without it. Without ssh tunneling, when dos attack was conduct to storage and fabric, all services (http/https, telnet and ssh) were down and client cannot access at all due to higher flow rate and goodput accepted by the interface of host target, filling up network resources. Applying ssh tunnel as intermediary system could reduce flow rate and goodput caused by dos attack.
- TT5222 - JARINGAN & PROTOKOL DATA
- CSH623 - TESIS
- TTH6M3 - KEAMANAN JARINGAN
- TTH6Z4 - TESIS
- IEH6B6 - TESIS
- TTI7Z4 - TESIS
- CII733 - TESIS
- IMI2B6 - TESIS
- CII733 - TESIS
- CII9H5 - PENELITIAN DISERTASI DAN SEMINAR 1
- CII9J5 - PENELITIAN DISERTASI DAN SEMINAR 2
- CII9L5 - PENELITIAN DISERTASI DAN SEMINAR 3
- CII9I1 - PENULISAN PUBLIKASI ILMIAH 1
- CII9K2 - PENULISAN PUBLIKASI ILMIAH 2
- CII9M3 - PENULISAN PUBLIKASI ILMIAH 3
Koleksi & Sirkulasi
Tersedia 1 dari total 1 Koleksi
Anda harus log in untuk mengakses flippingbook
Pengarang
| Nama | BUDHI HAMDANI |
| Jenis | Perorangan |
| Penyunting | DOAN PERDANA, ISTIKMAL |
| Penerjemah |
Penerbit
| Nama | Universitas Telkom |
| Kota | Bandung |
| Tahun | 2017 |
Sirkulasi
| Harga sewa | IDR 0,00 |
| Denda harian | IDR 0,00 |
| Jenis | Non-Sirkulasi |